About this infection
.RekenSom file ransomware malware is classified to be highly harmful because of its intention to lock your files. In short, it’s referred to as ransomware. There are various ways the threat may have entered your system, probably either through spam email attachments, infected adverts and downloads. We will further explain this in a further paragraph. Familiarize yourself with how ransomware spreads, because there could be severe results otherwise. It can be especially surprising to find your files encrypted if you have never encountered ransomware before, and you have little idea about what it is. Soon after you become aware of what’s going on, you will see a ransom message, which will reveal that so as to recover the files, you have to pay money. Remember who you are dealing with if you consider paying the ransom, because we doubt hackers will take the trouble to send you a decryption tool. It’s much more possible that you will be ignored after you make the payment than get a decryption tool. In addition, your money would support other malware projects in the future. You should also look into free decryptor available, a malicious software specialist could have been able to crack the ransomware and create a decryptor. Before making any rash decisions, carefully research the alternatives first. For those with backup available, simply remove .RekenSom file ransomware and then access the backup to restore files.
Download Removal Toolto remove .RekenSom file ransomware
Ransomware distribution ways
Your machine could have become infected in a couple of different ways, which we will discuss in a more detailed manner. Commonly, ransomware stick to quite simple methods in order to infect a device, but it is also probable you’ve gotten infected using more sophisticated ones. What we mean are ways sending spam emails or covering infections as legitimate downloads, essentially ones that only require minimum skill. You very likely got infected when you opened an email attachment that was harboring the ransomware. Hackers attach the ransomware to an email composed somewhat legitimately, and send it to hundreds or even thousands of potential victims, whose email addresses were sold by other cyber criminals. Normally, those emails have signs of being fake, but if you have never encountered them before, it may not be so. If the sender’s email address looks legitimate, or if the text is full of grammar mistakes, those might be signs that it’s a malicious email, particularly if you find it in your spam folder. Frequently, famous company names are used in the emails so that receivers lower their guard. So, as an example, if Amazon sends you an email, you still need to check whether the email address really belongs to the company. Check for your name used somewhere in the email, in the greeting for example, and if it isn’t, that should raise suspicion. Senders who claim to have some kind of business with you would be familiar with your name, thus common greetings like Sir/Madam, User or Customer wouldn’t be used. To be more specific, if you’re a customer of Amazon, the name you’ve provided them will be automatically put into emails they send you.
In short, just be more cautious when dealing with emails, which mostly means you shouldn’t rush to open the email attachments and ensure the sender is who you think it is. It is also not advisable to click on ads when visiting suspicious reputation websites. By engaging with an infected advert, you might end up permitting ransomware to download. The advertisements you encounter on those pages are certainly not reliable, they will only cause trouble. Downloading from untrustworthy sites may also bring about a contamination. If Torrents are what you use, at least only download torrents that were used by other users. There are also cases where vulnerabilities in software might be used for infection. So that those flaws can’t be used, you have to install the update as quickly as an update is released. You just need to install the fixes, which are released by software vendors when they become aware of the flaws.
What happened to your files
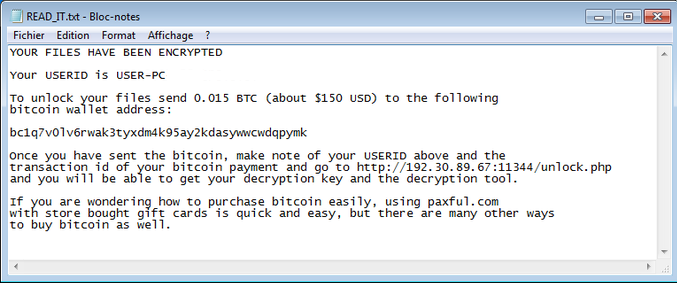
Your files will start being encrypted soon after you open the file infected with data encrypting malicious program. It targets documents, photos, videos, etc, virtually everything that could be of value to you. Once the files are located, they’ll be encrypted with a strong encryption algorithm. If you are not sure which files have been affected, the unusual file extensions attached to all locked ones will help you. A ransom note should then make itself known, which will offer you to buy a decryptor. You could be requested to pay a couple of thousands of dollars, or just $20, the amount depends on the ransomware. While we’ve already said our reasons for not recommending giving into the requests, in the end, the decision is yours. Looking into other options for file restoring would also be a good idea. There is some likelihood that researchers specializing in malicious software were successful in cracking the ransomware and thus were able to release a free decryption software. Maybe a backup is available and you simply do not remember it. Or maybe the ransomware left the Shadow copies of your files, which means they might be restorable using a certain application. We also hope you have learned your lesson and have invested into trustworthy backup. In case backup is an option, first eliminate .RekenSom file ransomware and then restore files.
.RekenSom file ransomware elimination
If you are not 100% sure with what you are doing, we don’t recommend you attempt manual elimination. If you do something incorrectly, irreversible harm could be caused to your computer. It would be better to use a malicious software elimination program because the software would do everything for you. The utility ought to successfully uninstall .RekenSom file ransomware as it was created with the intention of protecting your machine from such infections. However, do keep in mind that a malicious software elimination tool will not help with data restoring, it is not created to do that. You’ll have to look into how you can restore files yourself.
Download Removal Toolto remove .RekenSom file ransomware
Learn how to remove .RekenSom file ransomware from your computer
- Step 1. Remove .RekenSom file ransomware using Safe Mode with Networking.
- Step 2. Remove .RekenSom file ransomware using System Restore
- Step 3. Recover your data
Step 1. Remove .RekenSom file ransomware using Safe Mode with Networking.
a) Step 1. Access Safe Mode with Networking.
For Windows 7/Vista/XP
- Start → Shutdown → Restart → OK.

- Press and keep pressing F8 until Advanced Boot Options appears.
- Choose Safe Mode with Networking

For Windows 8/10 users
- Press the power button that appears at the Windows login screen. Press and hold Shift. Click Restart.

- Troubleshoot → Advanced options → Startup Settings → Restart.

- Choose Enable Safe Mode with Networking.

b) Step 2. Remove .RekenSom file ransomware.
You will now need to open your browser and download some kind of anti-malware software. Choose a trustworthy one, install it and have it scan your computer for malicious threats. When the ransomware is found, remove it. If, for some reason, you can't access Safe Mode with Networking, go with another option.Step 2. Remove .RekenSom file ransomware using System Restore
a) Step 1. Access Safe Mode with Command Prompt.
For Windows 7/Vista/XP
- Start → Shutdown → Restart → OK.

- Press and keep pressing F8 until Advanced Boot Options appears.
- Select Safe Mode with Command Prompt.

For Windows 8/10 users
- Press the power button that appears at the Windows login screen. Press and hold Shift. Click Restart.

- Troubleshoot → Advanced options → Startup Settings → Restart.

- Choose Enable Safe Mode with Command Prompt.

b) Step 2. Restore files and settings.
- You will need to type in cd restore in the window that appears. Press Enter.
- Type in rstrui.exe and again, press Enter.

- A window will pop-up and you should press Next. Choose a restore point and press Next again.

- Press Yes.
Step 3. Recover your data
While backup is essential, there is still quite a few users who do not have it. If you are one of them, you can try the below provided methods and you just might be able to recover files.a) Using Data Recovery Pro to recover encrypted files.
- Download Data Recovery Pro, preferably from a trustworthy website.
- Scan your device for recoverable files.

- Recover them.
b) Restore files through Windows Previous Versions
If you had System Restore enabled, you can recover files through Windows Previous Versions.- Find a file you want to recover.
- Right-click on it.
- Select Properties and then Previous versions.

- Pick the version of the file you want to recover and press Restore.
c) Using Shadow Explorer to recover files
If you are lucky, the ransomware did not delete your shadow copies. They are made by your system automatically for when system crashes.- Go to the official website (shadowexplorer.com) and acquire the Shadow Explorer application.
- Set up and open it.
- Press on the drop down menu and pick the disk you want.

- If folders are recoverable, they will appear there. Press on the folder and then Export.
* SpyHunter scanner, published on this site, is intended to be used only as a detection tool. More info on SpyHunter. To use the removal functionality, you will need to purchase the full version of SpyHunter. If you wish to uninstall SpyHunter, click here.

