How Recoverydatas file virus works
Recoverydatas file virus will immediately start encoding your files, since that’s the primary intention of ransomware. Ransomware is a very severe threat and could lead you to permanently losing your data. It’s very easy to get contaminated, which makes it a very dangerous malware. Spam email attachments, malicious adverts and fake downloads are the most typical reasons why ransomware can infect. After contamination, the encryption process begins, and once it’s finished, you will be asked to give money in exchange for a decryption. $50 or $1000 may be requested of you, it all depends on which ransomware you have. We do not suggest paying, no matter how little the sum is. Take into consideration that these are crooks you’re dealing with and they can just take your money and not give anything in exchange. If you take the time to look into it, you’ll definitely find accounts of people not being able to decrypt data, even after paying. Investing the demanded money into some backup option would be wiser. While you’ll be given a lot of different options, it shouldn’t be difficult to choose the best option for you. You may restore data after you erase Recoverydatas file virus if you had backup already prior to infection. Malware like this is lurking all over the place, and you’ll likely get contaminated again, so you need to be ready for it. In order to keep a system safe, one should always be on the lookout for possible threats, becoming informed about their spread methods.
Download Removal Toolto remove Recoverydatas file virus
How does data encoding malware spread
People usually infect their systems with data encoding malware by opening infected email attachments, pressing on infected ads and getting software from sources they shouldn’t. Nevertheless, that doesn’t mean more complicated methods will not be used by some file encrypting malicious software.
Remember if you have recently visited the spam section of your email inbox and downloaded a strange email attachment. All cyber criminals spreading the ransomware have to do is add an infected file to an email, send it to hundreds of people, and once the attachment is opened, the computer is infected. Those emails could seem urgent, usually including topics such as money, which is why people would open them without considering the danger of doing so. In addition to mistakes in grammar, if the sender, who certainly knows your name, uses Dear User/Customer/Member and firmly encourages you to open the attachment, it could be a sign that the email contains file encoding malware. To explain, if someone whose attachment you ought to open sends you an email, they would would know your name and would not use general greetings, and it wouldn’t end up in spam. You will also notice that criminals tend to use big names like Amazon so that people become more trusting. allowed the threat to infiltrate your device. If you were visiting a questionable or compromised website and pressed on an infected ad, it might have triggered the ransomware download. And stick to official pages for downloads. Bear in mind that you should never download anything, whether software or an update, from strange sources, such as ads. If a program was needed to be updated, you would be notified via the application itself, not via your browser, and most update without your intervention anyway.
What happened to your files?
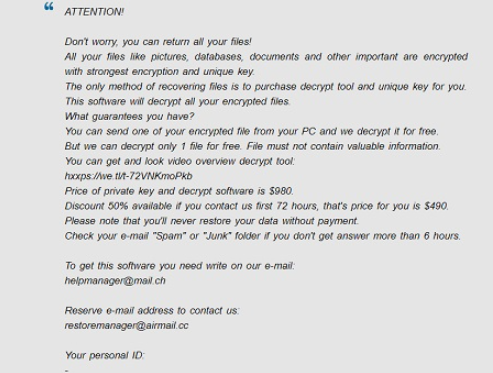
An infection might result in your files being permanently encrypted, which is what makes it such a dangerous threat. The process of encoding your data take a very short time, so you may not even notice it. If not for other signs, you will notice the data encoding malicious program when weird file extension appear attached to your files. The reason why your files might be permanently lost is because some ransomware use strong encryption algorithms for the encryption process, and it is not always possible to break them. In case you don’t understand what has happened, a ransom note should explain everything. The creators/distributors of the data encrypting malware will offer you a decryption utility, which you obviously have to pay for, and that isn’t advised. The crooks might just take your money, they won’t feel obligated to aid you. The ransom money would also possibly be financing future ransomware or other malicious software projects. And, people will increasingly become interested in the already highly profitable business, which allegedly made $1 billion in 2016 alone. We would advise investing in a backup option, which would always be there in case you lost your original files. These types of infections could reoccur again, but if backup was available, file loss would not be a possibility. We would suggest you ignore the requests, and if the infection is still inside on your computer, remove Recoverydatas file virus, for which you’ll see guidelines below. These kinds threats can be avoided, if you know how they spread, so try to become familiar with its distribution methods, in detail.
How to remove Recoverydatas file virus
Bear in mind that malicious program removal software will be needed to fully get rid of the ransomware. Because you need to know exactly what you are doing, we do not advise proceeding to remove Recoverydatas file virus manually. If you implement anti-malware software, you wouldn’t be risking doing more harm to your system. Malicious threat removal programs are made to erase Recoverydatas file virus and all other similar infections, so you should not encounter any problems. You can find guidelines to help you, if you aren’t sure where to begin. Keep in mind that the program cannot help you decrypt your data, all it will do is take care of the infection. However, free decryption utilities are released by malware specialists, if the ransomware is decryptable.
Download Removal Toolto remove Recoverydatas file virus
Learn how to remove Recoverydatas file virus from your computer
- Step 1. Remove Recoverydatas file virus using Safe Mode with Networking.
- Step 2. Remove Recoverydatas file virus using System Restore
- Step 3. Recover your data
Step 1. Remove Recoverydatas file virus using Safe Mode with Networking.
a) Step 1. Access Safe Mode with Networking.
For Windows 7/Vista/XP
- Start → Shutdown → Restart → OK.

- Press and keep pressing F8 until Advanced Boot Options appears.
- Choose Safe Mode with Networking

For Windows 8/10 users
- Press the power button that appears at the Windows login screen. Press and hold Shift. Click Restart.

- Troubleshoot → Advanced options → Startup Settings → Restart.

- Choose Enable Safe Mode with Networking.

b) Step 2. Remove Recoverydatas file virus.
You will now need to open your browser and download some kind of anti-malware software. Choose a trustworthy one, install it and have it scan your computer for malicious threats. When the ransomware is found, remove it. If, for some reason, you can't access Safe Mode with Networking, go with another option.Step 2. Remove Recoverydatas file virus using System Restore
a) Step 1. Access Safe Mode with Command Prompt.
For Windows 7/Vista/XP
- Start → Shutdown → Restart → OK.

- Press and keep pressing F8 until Advanced Boot Options appears.
- Select Safe Mode with Command Prompt.

For Windows 8/10 users
- Press the power button that appears at the Windows login screen. Press and hold Shift. Click Restart.

- Troubleshoot → Advanced options → Startup Settings → Restart.

- Choose Enable Safe Mode with Command Prompt.

b) Step 2. Restore files and settings.
- You will need to type in cd restore in the window that appears. Press Enter.
- Type in rstrui.exe and again, press Enter.

- A window will pop-up and you should press Next. Choose a restore point and press Next again.

- Press Yes.
Step 3. Recover your data
While backup is essential, there is still quite a few users who do not have it. If you are one of them, you can try the below provided methods and you just might be able to recover files.a) Using Data Recovery Pro to recover encrypted files.
- Download Data Recovery Pro, preferably from a trustworthy website.
- Scan your device for recoverable files.

- Recover them.
b) Restore files through Windows Previous Versions
If you had System Restore enabled, you can recover files through Windows Previous Versions.- Find a file you want to recover.
- Right-click on it.
- Select Properties and then Previous versions.

- Pick the version of the file you want to recover and press Restore.
c) Using Shadow Explorer to recover files
If you are lucky, the ransomware did not delete your shadow copies. They are made by your system automatically for when system crashes.- Go to the official website (shadowexplorer.com) and acquire the Shadow Explorer application.
- Set up and open it.
- Press on the drop down menu and pick the disk you want.

- If folders are recoverable, they will appear there. Press on the folder and then Export.
* SpyHunter scanner, published on this site, is intended to be used only as a detection tool. More info on SpyHunter. To use the removal functionality, you will need to purchase the full version of SpyHunter. If you wish to uninstall SpyHunter, click here.

