Is Banjo ransomware a dangerous infection
Banjo ransomware will encrypt your data and request that you pay for a decryption key. Infecting a system with ransomware can lead to permanent file encryption, which is why it’s regarded as such a harmful threat. Certain files will be encrypted soon after the ransomware is launched. Photos, videos and documents are the usually targeted files due to their value to victims. You will need to get a specialized decryption key to decrypt files but sadly, the criminals who encrypted your files have it. The good news is that ransomware is every now and then cracked by malware specialists, and they may release a free decryption application. We cannot be sure a decryption tool will be created but that might be your only option if backup has not been made.
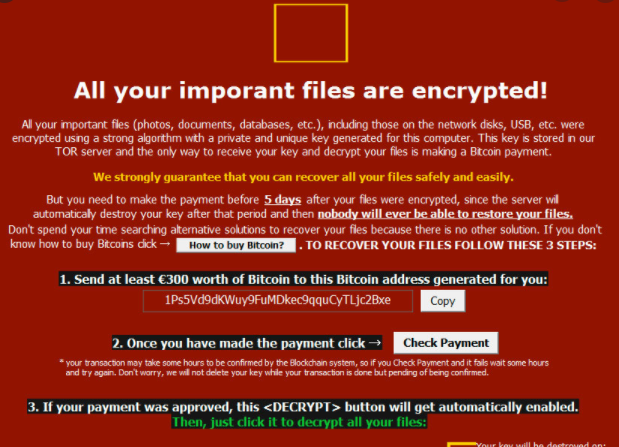
Soon after you become aware of the situation, you will notice a ransom note. The note you will find ought to contain an explanation about what happened to your files and how much you should pay to get them back. It isn’t unexpected but paying hackers is not something we advise. Crooks simply taking your money and not helping you recover files isn’t a surprising scenario. More malicious software would be developed using that money. Consider using that money to purchase backup. Simply terminate Banjo ransomware if you do have backup.
If you recall opening a strange email attachment or downloading some kind of update, that is how you could have infected your system. These are two of the most common methods to distribute this kind of malware.
Download Removal Toolto remove Banjo ransomwareRansomware spread ways
Though your device could get infected in many ways, you probably got it via spam email or bogus update. If you remember opening a weird email attachment, you have to be more cautious. Always attentively check the email before opening the file attached. In a lot of such emails, known company names are used because that would provide a sense of security to users. For example, they could pretend to be Amazon and say that they have added a receipt for a recent purchase to the email. You could check whether the sender is actually who they say they are without difficulty. All you actually have to do is see if the email address matches any that belong to the company. If you have any doubts, you also need to scan the attachment with a reliable malicious software scanner, just to be sure.
Malicious software updates could have also been how you got the ransomware. Dubious sites are the most probable place where you could have encountered the false update notifications. Frequently, the false update notifications could appear in banner or advertisement form. Though people who are familiar with how updates work will never fall for it as they are rather obviously bogus. You ought to never download updates or programs from sources like adverts. If you have set automatic updates, you will not even be alerted about it, but if manual update is needed, you’ll be alerted via the application itself.
How does ransomware behave
As is probably clear by now, certain files kept on your system have been encrypted. As soon as the infected file was opened, the encryption began, and you could have missed it. A weird extension will be added to all affected files. As a powerful encryption algorithm was used to encrypt files, don’t waste your time attempting to open files. A ransom notification will then appear and it’ll explain what to do about recovering files. Text files that act as the ransom note generally threaten users with eliminated files and strongly encourage victims to buy the offered decryptor. It’s possible that criminals behind this ransomware have the sole decryptor but despite that, paying the ransom isn’t recommended. Even after you make a payment, we doubt that cyber criminals will feel obligated to aid you. Hackers may also remember that you paid and target you again, thinking you’ll pay again.
You should first try and recall whether you’ve stored any of your files somewhere. In case malicious software researchers are able to develop a free decryption tool in the future, backup all your encrypted files. It’s essential that you remove Banjo ransomware from your system as soon as possible, whatever the case may be.
We expect this experience will be a lesson, and you will begin routinely backing up your files. Since the risk of losing your files never goes away, take our advice. Quite a few backup options are available, and they are well worth the purchase if you do not wish to lose your files.
Banjo ransomware removal
If you’re reading this, manual removal is probably not for you. Acquire anti-malware to erase the ransomware, instead. If you are having trouble running the program, attempt again after rebooting your computer in Safe Mode. There should be no issues when your run the software, so you could successfully terminate Banjo ransomware. Sadly, malware removal program won’t capable of helping with file decryption, it’ll simply just take care of the malware’s removal.
Download Removal Toolto remove Banjo ransomware
Learn how to remove Banjo ransomware from your computer
- Step 1. Remove Banjo ransomware using Safe Mode with Networking.
- Step 2. Remove Banjo ransomware using System Restore
- Step 3. Recover your data
Step 1. Remove Banjo ransomware using Safe Mode with Networking.
a) Step 1. Access Safe Mode with Networking.
For Windows 7/Vista/XP
- Start → Shutdown → Restart → OK.

- Press and keep pressing F8 until Advanced Boot Options appears.
- Choose Safe Mode with Networking

For Windows 8/10 users
- Press the power button that appears at the Windows login screen. Press and hold Shift. Click Restart.

- Troubleshoot → Advanced options → Startup Settings → Restart.

- Choose Enable Safe Mode with Networking.

b) Step 2. Remove Banjo ransomware.
You will now need to open your browser and download some kind of anti-malware software. Choose a trustworthy one, install it and have it scan your computer for malicious threats. When the ransomware is found, remove it. If, for some reason, you can't access Safe Mode with Networking, go with another option.Step 2. Remove Banjo ransomware using System Restore
a) Step 1. Access Safe Mode with Command Prompt.
For Windows 7/Vista/XP
- Start → Shutdown → Restart → OK.

- Press and keep pressing F8 until Advanced Boot Options appears.
- Select Safe Mode with Command Prompt.

For Windows 8/10 users
- Press the power button that appears at the Windows login screen. Press and hold Shift. Click Restart.

- Troubleshoot → Advanced options → Startup Settings → Restart.

- Choose Enable Safe Mode with Command Prompt.

b) Step 2. Restore files and settings.
- You will need to type in cd restore in the window that appears. Press Enter.
- Type in rstrui.exe and again, press Enter.

- A window will pop-up and you should press Next. Choose a restore point and press Next again.

- Press Yes.
Step 3. Recover your data
While backup is essential, there is still quite a few users who do not have it. If you are one of them, you can try the below provided methods and you just might be able to recover files.a) Using Data Recovery Pro to recover encrypted files.
- Download Data Recovery Pro, preferably from a trustworthy website.
- Scan your device for recoverable files.

- Recover them.
b) Restore files through Windows Previous Versions
If you had System Restore enabled, you can recover files through Windows Previous Versions.- Find a file you want to recover.
- Right-click on it.
- Select Properties and then Previous versions.

- Pick the version of the file you want to recover and press Restore.
c) Using Shadow Explorer to recover files
If you are lucky, the ransomware did not delete your shadow copies. They are made by your system automatically for when system crashes.- Go to the official website (shadowexplorer.com) and acquire the Shadow Explorer application.
- Set up and open it.
- Press on the drop down menu and pick the disk you want.

- If folders are recoverable, they will appear there. Press on the folder and then Export.
* SpyHunter scanner, published on this site, is intended to be used only as a detection tool. More info on SpyHunter. To use the removal functionality, you will need to purchase the full version of SpyHunter. If you wish to uninstall SpyHunter, click here.

