Get rid of Horsuke ransomware
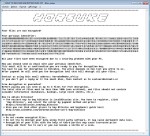 Horsuke ransomware ransomware is a piece of malicious software that'll encode your files. It's a highly serious infection that could leave you with encrypted data and no way to get them back. Also it is quite easy to contaminate your device. If your system is infected, it is quite probably you opened a spam email attachment, clicked on an infected ad or fell for a bogus download. After it encodes your data, it'll request that you pay a certain amount of money for a for a way to decode files. The money you are requested to pay will probably range from $100 to $1000, depending on which ransomware you have. Whatever you are demanded to pay by this threat, consider every possible consequence before you do. Who is going to stop criminals from taking your money, providing nothing in return. You can certainly find accounts of people not being able to recover files after payment, and that is not really shocking. This type of thing may reoccur or your system may crash, so it would be better to invest the money into some kind of backup. There are many options, and we are sure you will find one best suiting your needs. For those who did take the time to make copies of the files prior to contamination, simply uninstall Horsuke ransomware and then proceed to restore data from where you're storing them. This isn't the last time you will get contaminated with some kind of malware, so you ought to prepare. If you wish your device to be malware-free, you will have to learn about malicious software and how it could enter your computer.
Read more...
Horsuke ransomware ransomware is a piece of malicious software that'll encode your files. It's a highly serious infection that could leave you with encrypted data and no way to get them back. Also it is quite easy to contaminate your device. If your system is infected, it is quite probably you opened a spam email attachment, clicked on an infected ad or fell for a bogus download. After it encodes your data, it'll request that you pay a certain amount of money for a for a way to decode files. The money you are requested to pay will probably range from $100 to $1000, depending on which ransomware you have. Whatever you are demanded to pay by this threat, consider every possible consequence before you do. Who is going to stop criminals from taking your money, providing nothing in return. You can certainly find accounts of people not being able to recover files after payment, and that is not really shocking. This type of thing may reoccur or your system may crash, so it would be better to invest the money into some kind of backup. There are many options, and we are sure you will find one best suiting your needs. For those who did take the time to make copies of the files prior to contamination, simply uninstall Horsuke ransomware and then proceed to restore data from where you're storing them. This isn't the last time you will get contaminated with some kind of malware, so you ought to prepare. If you wish your device to be malware-free, you will have to learn about malicious software and how it could enter your computer.
Read more...
Delete Rapid 3.0 ransomware
 Rapid 3.0 ransomware is a file-encoding kind of malicious program, which is often called ransomware. These types of contaminations aren't be taken lightly, as they might result in file loss. It's quite easy to get infected, which only adds to why it's so dangerous. If you have recently opened a weird email attachment, pressed on a dubious advert or downloaded an application advertised on some untrustworthy web page, that's how it infected your system. After it encrypts your files, it will request you to pay a certain amount of money for a decryptor. The sum you are asked to pay is likely to differ depending on the type of file encrypting malware has infiltrated your computer, but should range from $50 to possibly thousands of dollars. No matter how much you're requested to pay, giving into the demands isn't something we advise doing. Consider whether you'll actually get your data back after payment, considering you cannot prevent criminals from just taking your money. If your data still remains encrypted after paying, you would definitely not be the first one. This could easily occur again, so consider buying backup, instead of giving into the demands. From external hard drives to cloud storage, there are plenty of backup options out there, you simply need to choose the one best suiting your needs. For those who did back up files before the malicious software got in, simply terminate Rapid 3.0 ransomware and recover data from where you are keeping them. These threats won't go away any time soon, so you need to be prepared. To keep a device safe, one should always be ready to come across possible threats, becoming familiar with how to avoid them.
Read more...
Rapid 3.0 ransomware is a file-encoding kind of malicious program, which is often called ransomware. These types of contaminations aren't be taken lightly, as they might result in file loss. It's quite easy to get infected, which only adds to why it's so dangerous. If you have recently opened a weird email attachment, pressed on a dubious advert or downloaded an application advertised on some untrustworthy web page, that's how it infected your system. After it encrypts your files, it will request you to pay a certain amount of money for a decryptor. The sum you are asked to pay is likely to differ depending on the type of file encrypting malware has infiltrated your computer, but should range from $50 to possibly thousands of dollars. No matter how much you're requested to pay, giving into the demands isn't something we advise doing. Consider whether you'll actually get your data back after payment, considering you cannot prevent criminals from just taking your money. If your data still remains encrypted after paying, you would definitely not be the first one. This could easily occur again, so consider buying backup, instead of giving into the demands. From external hard drives to cloud storage, there are plenty of backup options out there, you simply need to choose the one best suiting your needs. For those who did back up files before the malicious software got in, simply terminate Rapid 3.0 ransomware and recover data from where you are keeping them. These threats won't go away any time soon, so you need to be prepared. To keep a device safe, one should always be ready to come across possible threats, becoming familiar with how to avoid them.
Read more...
Get rid of Ransomed@india ransomware
 Ransomed@india ransomware is considered to be ransomware, a kind of malware that will lock your files. It's a severe threat that could leave you with encoded files and no way to restore them. Because of this, and the fact that getting infected is quite easy, file encrypting malware is thought to be very dangerous. Infection may happen via spam email attachments, infected adverts or bogus downloads. As soon as the encryption process has been completed, you'll see a ransom note, requesting money in exchange for a tool to decrypt your files. You'll probably be demanded to pay between tens and thousands of dollars, depending on what file encoding malware you have, and how much you value your data. Consider everything carefully before agreeing to pay, no matter how little money it demands. We highly doubt criminals will have a moral obligation to return your files, so they can just take your money. You would not be the first person to get nothing. Backup is a better investment, because you would not jeopardizing your data if the situation were to reoccur. You can find all kinds of backup options, and we're sure you will be able to find one that is right for you. If you had backup prior to infection, data recovery will be possible after you terminate Ransomed@india ransomware. These types of contaminations are everywhere, so you need to be ready. In order to keep a computer safe, one should always be ready to encounter possible malware, becoming familiar with how to avoid them.
Read more...
Ransomed@india ransomware is considered to be ransomware, a kind of malware that will lock your files. It's a severe threat that could leave you with encoded files and no way to restore them. Because of this, and the fact that getting infected is quite easy, file encrypting malware is thought to be very dangerous. Infection may happen via spam email attachments, infected adverts or bogus downloads. As soon as the encryption process has been completed, you'll see a ransom note, requesting money in exchange for a tool to decrypt your files. You'll probably be demanded to pay between tens and thousands of dollars, depending on what file encoding malware you have, and how much you value your data. Consider everything carefully before agreeing to pay, no matter how little money it demands. We highly doubt criminals will have a moral obligation to return your files, so they can just take your money. You would not be the first person to get nothing. Backup is a better investment, because you would not jeopardizing your data if the situation were to reoccur. You can find all kinds of backup options, and we're sure you will be able to find one that is right for you. If you had backup prior to infection, data recovery will be possible after you terminate Ransomed@india ransomware. These types of contaminations are everywhere, so you need to be ready. In order to keep a computer safe, one should always be ready to encounter possible malware, becoming familiar with how to avoid them.
Read more...
Delete KCW ransomware
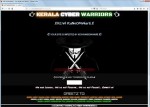 KCW ransomware is a malware that will encode your files, most commonly known as ransomware. Ransomware is classified to be a very serious contamination as you could end up permanently losing access to your files. Additionally, contaminating a system is very easy, thus making file encrypting malware a highly dangerous threat. If your computer is infected, a spam email attachment, an infected ad or a bogus download is responsible. Once the encryption process is completed, a ransom note will appear, decryptor. You will likely be asked to pay between tens and thousands of dollars, it depends on what ransomware you have, and how much you value your data. No matter how much you are requested to pay, we don't advise complying with the demands. Considering crooks will not feel obligated to recover your files, what is preventing them from taking your money and not giving anything in return. You certainly wouldn't be the first person to be left with no recovered files after payment. This could easily reoccur, so instead of complying with the demands, consider buying backup. You will find all types of backup options, and we are certain you will be able to find one that is right for you. Just eliminate KCW ransomware, and if you had backup prior to infection, file recovery should not cause issues. These types of threats are everywhere, so you need to prepare yourself. If you wish to remain safe, you need to become familiar with possible contaminations and how to protect yourself.
Read more...
KCW ransomware is a malware that will encode your files, most commonly known as ransomware. Ransomware is classified to be a very serious contamination as you could end up permanently losing access to your files. Additionally, contaminating a system is very easy, thus making file encrypting malware a highly dangerous threat. If your computer is infected, a spam email attachment, an infected ad or a bogus download is responsible. Once the encryption process is completed, a ransom note will appear, decryptor. You will likely be asked to pay between tens and thousands of dollars, it depends on what ransomware you have, and how much you value your data. No matter how much you are requested to pay, we don't advise complying with the demands. Considering crooks will not feel obligated to recover your files, what is preventing them from taking your money and not giving anything in return. You certainly wouldn't be the first person to be left with no recovered files after payment. This could easily reoccur, so instead of complying with the demands, consider buying backup. You will find all types of backup options, and we are certain you will be able to find one that is right for you. Just eliminate KCW ransomware, and if you had backup prior to infection, file recovery should not cause issues. These types of threats are everywhere, so you need to prepare yourself. If you wish to remain safe, you need to become familiar with possible contaminations and how to protect yourself.
Read more...
Get rid of PSCrypt ransomware
 PSCrypt ransomware is a file-encoding ransomware type of virus that critical piece of malicious program, known as ransomware, that is capable of encoding your files. aggressive file-encoding software viruses are extremely harmful computer infections as they encode files and proceed to ask. We should caution you that pretty often, users don't get their files back their files. You probably opened a dangerous email attachment or fell for a fake download recently and that is how you your computer contaminated. These kinds of things are what specialists are alerting users about again and again. When users bump into ransomware, developers ask that they pay a ransom, which isn't something you should do, in our view. It would actually be shocking if you got your data unlocked after payment, because criminals don't feel obliged to help you. Do not give into the demands, and just terminate PSCrypt ransomware.
Read more...
PSCrypt ransomware is a file-encoding ransomware type of virus that critical piece of malicious program, known as ransomware, that is capable of encoding your files. aggressive file-encoding software viruses are extremely harmful computer infections as they encode files and proceed to ask. We should caution you that pretty often, users don't get their files back their files. You probably opened a dangerous email attachment or fell for a fake download recently and that is how you your computer contaminated. These kinds of things are what specialists are alerting users about again and again. When users bump into ransomware, developers ask that they pay a ransom, which isn't something you should do, in our view. It would actually be shocking if you got your data unlocked after payment, because criminals don't feel obliged to help you. Do not give into the demands, and just terminate PSCrypt ransomware.
Read more...
Remove Sepsis ransomware
 Sepsis ransomware file-encoding malware, often known as ransomware, will encode your data. It's not a light infection as it could leave you with no way to restore your files. What's worse is that it is fairly easy to infect your computer. A big factor in a successful ransomware infection is user negligence, as contamination generally infects through spam email attachments, contaminated adverts and malicious downloads. Once the encoding process is finished, you'll get a ransom note, decryptor. Depending on what kind of file encoding malicious program you have, the sum requested will be different. Complying with the demands isn't something you ought to do, so consider all scenarios. Considering crooks will feel no obligation to help you in file recovery, we doubt they will not just take your money. If you take the time to look into it, you'll definitely find accounts of users not being able to recover data, even after paying. Backup is a far better investment, since you wouldn't endangering your data if the situation were to reoccur. You can find all kinds of backup options, and we're certain you will be able to find one that's right for you. If backup was made prior to you contaminating your machine, you will be able to restore files after you remove Sepsis ransomware. These kinds of contaminations are hiding everywhere, so you need to prepare yourself. If you wish to remain safe, you have to familiarize yourself with likely contaminations and how to shield your device from them.
Read more...
Sepsis ransomware file-encoding malware, often known as ransomware, will encode your data. It's not a light infection as it could leave you with no way to restore your files. What's worse is that it is fairly easy to infect your computer. A big factor in a successful ransomware infection is user negligence, as contamination generally infects through spam email attachments, contaminated adverts and malicious downloads. Once the encoding process is finished, you'll get a ransom note, decryptor. Depending on what kind of file encoding malicious program you have, the sum requested will be different. Complying with the demands isn't something you ought to do, so consider all scenarios. Considering crooks will feel no obligation to help you in file recovery, we doubt they will not just take your money. If you take the time to look into it, you'll definitely find accounts of users not being able to recover data, even after paying. Backup is a far better investment, since you wouldn't endangering your data if the situation were to reoccur. You can find all kinds of backup options, and we're certain you will be able to find one that's right for you. If backup was made prior to you contaminating your machine, you will be able to restore files after you remove Sepsis ransomware. These kinds of contaminations are hiding everywhere, so you need to prepare yourself. If you wish to remain safe, you have to familiarize yourself with likely contaminations and how to shield your device from them.
Read more...
Erase Facebook ransomware
 Facebook ransomware is a really severe infection, known as ransomware or file-encrypting malicious program. If ransomware was unknown to you until now, you may be in for a surprise. File encrypting malware uses powerful encryption algorithms to encode data, and once it is done carrying out the process, data will be locked and you'll be unable to access them. Ransomware is classified as a very dangerous threat because decrypting files might be not possible. There's the option of paying pay crooks for a decryptor, but we do not suggest that. First of all, you might be just spending your money because payment doesn't always lead to file decryption. Consider what's preventing crooks from just taking your money. You ought to also keep in mind that the money will be used for malware projects in the future. Data encrypting malware is already costing millions of dollars to businesses, do you really want to support that. People are also becoming increasingly attracted to the industry because the more people give into the requests, the more profitable it becomes. You might find yourself in this kind of situation again in the future, so investing the demanded money into backup would be better because you wouldn't need to worry about losing your files. If backup was made before your computer got infected, erase Facebook ransomware virus and proceed to data recovery. You may find details on how to shield your device from an infection in the following paragraph, in case you're unsure about how the ransomware managed to infect your computer. Read more...
Facebook ransomware is a really severe infection, known as ransomware or file-encrypting malicious program. If ransomware was unknown to you until now, you may be in for a surprise. File encrypting malware uses powerful encryption algorithms to encode data, and once it is done carrying out the process, data will be locked and you'll be unable to access them. Ransomware is classified as a very dangerous threat because decrypting files might be not possible. There's the option of paying pay crooks for a decryptor, but we do not suggest that. First of all, you might be just spending your money because payment doesn't always lead to file decryption. Consider what's preventing crooks from just taking your money. You ought to also keep in mind that the money will be used for malware projects in the future. Data encrypting malware is already costing millions of dollars to businesses, do you really want to support that. People are also becoming increasingly attracted to the industry because the more people give into the requests, the more profitable it becomes. You might find yourself in this kind of situation again in the future, so investing the demanded money into backup would be better because you wouldn't need to worry about losing your files. If backup was made before your computer got infected, erase Facebook ransomware virus and proceed to data recovery. You may find details on how to shield your device from an infection in the following paragraph, in case you're unsure about how the ransomware managed to infect your computer. Read more...
Delete StalinLocker ransomware
 StalinLocker ransomware will lock your files, since that is the prime intention of ransomware. It really depends on which ransomware is to blame, but you may end up permanently losing your data. Another reason why it's considered to be a highly damaging malicious software is that the infection is rather easy to obtain. People most often get infected via spam emails, infected adverts or bogus downloads. Once the ransomware is finished encoding your files, you'll get a ransom note, decryptor utility. The amount of money demanded varies from ransomware to ransomware, some demand $1000 or more, some may settle with $100. Even if you are demanded to pay a small amount, we do not suggest giving in. It is not 100% guaranteed you will get your data back, even after paying, considering you cannot stop criminals from simply taking your money. It would not be shocking if you're left with encrypted files, and you would certainly not be the only one. Investing the money you're asked for into dependable backup would be wiser. There are plenty of options to choose from, and we are sure you will find one best suiting your needs. You can restore files from backup if you had it done prior to infection, after you uninstall StalinLocker ransomware. These threats are not going away any time soon, so you will have to prepare yourself. If you wish to stay safe, you need to become familiar with possible threats and how to protect your machine from them.
Read more...
StalinLocker ransomware will lock your files, since that is the prime intention of ransomware. It really depends on which ransomware is to blame, but you may end up permanently losing your data. Another reason why it's considered to be a highly damaging malicious software is that the infection is rather easy to obtain. People most often get infected via spam emails, infected adverts or bogus downloads. Once the ransomware is finished encoding your files, you'll get a ransom note, decryptor utility. The amount of money demanded varies from ransomware to ransomware, some demand $1000 or more, some may settle with $100. Even if you are demanded to pay a small amount, we do not suggest giving in. It is not 100% guaranteed you will get your data back, even after paying, considering you cannot stop criminals from simply taking your money. It would not be shocking if you're left with encrypted files, and you would certainly not be the only one. Investing the money you're asked for into dependable backup would be wiser. There are plenty of options to choose from, and we are sure you will find one best suiting your needs. You can restore files from backup if you had it done prior to infection, after you uninstall StalinLocker ransomware. These threats are not going away any time soon, so you will have to prepare yourself. If you wish to stay safe, you need to become familiar with possible threats and how to protect your machine from them.
Read more...
Remove FBLocker ransomware
 FBLocker ransomware file-encoding malware, generally known as ransomware, will encrypt your files. These types of infections should be taken seriously, as they could result in file loss. What's more, contaminating a system is very easy, therefore making data encrypting malware a highly dangerous contamination. People most often get infected through spam emails, infected advertisements or bogus downloads. Once the data encoding malware is done encoding your files, a ransom note will pop up, decryptor. Between $100 and $1000 is probably what you'll be asked to pay. It isn't recommended to pay, even if you are requested for a small sum. We very much doubt cyber crooks will have a moral obligation to return your files, so you might just end up wasting your money. You can definitely encounter accounts of people not getting files back after payment, and that is not really surprising. Consider investing the money into backup, so that if this were to happen again, you wouldn't lose your files. You will find all kinds of backup options, and we are sure you can find one that's right for you. For those who did back up files before the malicious software invaded, simply remove FBLocker ransomware and recover data from where they're kept. This isn't the last time you'll get infected with some kind of malware, so you have to be ready. If you wish your system to be infection-free, it is vital to learn about malicious programs and how it could infiltrate your system.
Read more...
FBLocker ransomware file-encoding malware, generally known as ransomware, will encrypt your files. These types of infections should be taken seriously, as they could result in file loss. What's more, contaminating a system is very easy, therefore making data encrypting malware a highly dangerous contamination. People most often get infected through spam emails, infected advertisements or bogus downloads. Once the data encoding malware is done encoding your files, a ransom note will pop up, decryptor. Between $100 and $1000 is probably what you'll be asked to pay. It isn't recommended to pay, even if you are requested for a small sum. We very much doubt cyber crooks will have a moral obligation to return your files, so you might just end up wasting your money. You can definitely encounter accounts of people not getting files back after payment, and that is not really surprising. Consider investing the money into backup, so that if this were to happen again, you wouldn't lose your files. You will find all kinds of backup options, and we are sure you can find one that's right for you. For those who did back up files before the malicious software invaded, simply remove FBLocker ransomware and recover data from where they're kept. This isn't the last time you'll get infected with some kind of malware, so you have to be ready. If you wish your system to be infection-free, it is vital to learn about malicious programs and how it could infiltrate your system.
Read more...
Get rid of RansomAES ransomware
 RansomAES ransomware ransomware is a piece of malware that will encrypt your files. You've got a very serious infection on your hands, and it may lead to severe trouble, such as permanent file loss. Also it is fairly easy to infect your device. If you have it, you likely opened a spam email attachment, pressed on a malicious advertisement or fell for a fake download. After data is successfully encrypted, it'll ask you to pay a ransom for a decryptor. How much is demanded of you depends on the ransomware, some ask for thousands of dollars, some for much less. Before rushing to pay, take a couple of things into consideration. Do not trust crooks to keep their word and restore your data, because they can simply take your money. If you were left with still locked data after paying, you would certainly not be the first one. This could easily occur again, so consider buying backup, instead of complying with the demands. We are sure you can find an option that suits your needs as there are many to choose from. If backup is available, as soon you remove RansomAES ransomware, there should not be an issue when recovering data after you erase RansomAES ransomware. These kinds of threats aren't going away in the foreseeable future, so you will have to prepare yourself. If you want to remain safe, you have to familiarize yourself with possible contaminations and how to shield yourself.
Read more...
RansomAES ransomware ransomware is a piece of malware that will encrypt your files. You've got a very serious infection on your hands, and it may lead to severe trouble, such as permanent file loss. Also it is fairly easy to infect your device. If you have it, you likely opened a spam email attachment, pressed on a malicious advertisement or fell for a fake download. After data is successfully encrypted, it'll ask you to pay a ransom for a decryptor. How much is demanded of you depends on the ransomware, some ask for thousands of dollars, some for much less. Before rushing to pay, take a couple of things into consideration. Do not trust crooks to keep their word and restore your data, because they can simply take your money. If you were left with still locked data after paying, you would certainly not be the first one. This could easily occur again, so consider buying backup, instead of complying with the demands. We are sure you can find an option that suits your needs as there are many to choose from. If backup is available, as soon you remove RansomAES ransomware, there should not be an issue when recovering data after you erase RansomAES ransomware. These kinds of threats aren't going away in the foreseeable future, so you will have to prepare yourself. If you want to remain safe, you have to familiarize yourself with possible contaminations and how to shield yourself.
Read more...