What is file encrypting malware
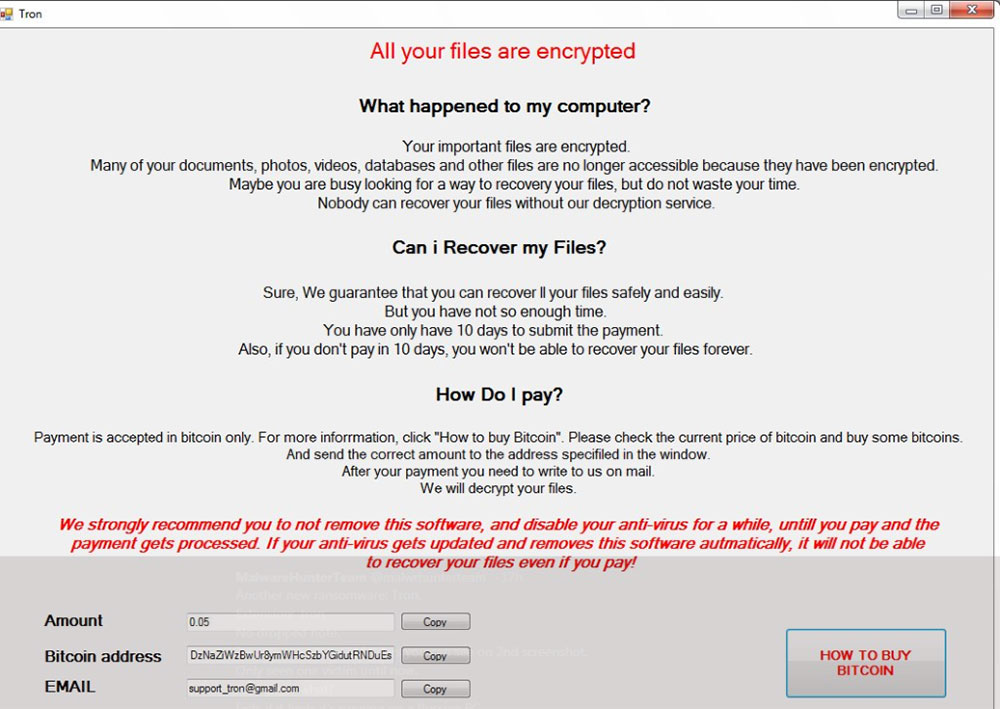
Tron Ransomware file-encoding malicious program, more commonly known as ransomware, will encode your data. Infection may mean, you may permanently lose access to your files, so do take the infection seriously. It’s pretty easy to contaminate your device, which makes it a very dangerous malicious software. If you recall opening a strange email attachment, clicking on some dubious ad or downloading an application promoted on some untrustworthy site, that is how it infected your device. After infection, the encryption process begins, and once it is completed, you’ll be requested to pay a specific sum of money if you want to recover your files. $50 or $1000 could be requested of you, depending on which ransomware you have. Whether you are asked for a lot of money, or a small amount, complying with the demands isn’t suggested. Consider whether you’ll actually get your data back after payment, considering there’s nothing preventing criminals from simply taking your money. If your files still remains locked after paying, it would not be that surprising. Research backup options, so that if this situation was to occur again, you wouldn’t lose your files. You’ll be presented with a lot of different options, but it shouldn’t be difficult to find the best option for you. Just terminate Tron Ransomware, and if you had backup before the infection, you ought to be able to recover files from there. You’ll run into malware like this everywhere, and you will likely get contaminated again, so you have to be prepared for it. In order to keep a system safe, one must always be ready to run into possible malware, becoming familiar with how to avoid them.
Download Removal Toolto remove Tron Ransomware
How does ransomware spread
People usually get ransomware by opening infected email attachments, engaging with infected adverts and downloading from sources they shouldn’t. That doesn’t mean creators won’t use elaborate methods.
If you recall downloading a strange attachment from an apparently real email in the spam folder, that may be where you got the file encoding malware from. Criminals distributing ransomware add a corrupted file to an email, send it to potential victims, who infect their devices as soon as they open the attachment. It is not rare for those emails to contain money-related info, which alarms users into opening it. When dealing with unknown sender emails, be on the look out for certain signs that it might be harboring file encoding malware, like mistakes in grammar, encourage to open the attachment. A company whose email is vital enough to open would not use general greetings, and would instead write your name. You might see company names like Amazon or PayPal used in those emails, as known names would make people trust the email more. Clicking on adverts when on dubious websites and downloading files from unreliable sources could also lead to an infection. If you frequently engage with advertisements while on dubious sites, it is no wonder you got your system contaminated. Or you may have downloaded a ransomware-infected file from an unreliable source. One thing to remember is to never download programs, updates, or anything really, from pop-up or any other kinds of advertisements. If an application needed to update itself, it would do it itself or alert you, but never through browser.
What happened to your files?
It is possible for a file encoding malicious software to permanently encrypt files, which is why it is such a harmful threat to have. Once it’s inside, it will take minutes, if not seconds to find the files it wants and encode them. All encoding files will have a file extension attached to them. The reason why your files might be not possible to decode for free is because some file encoding malware use strong encryption algorithms for the encoding process, and may be impossible to break them. A note with the ransom will then appear on your screen, or will be found in folders containing encoded files, and it should give you a general idea of what is going on. The note will demand that you pay for a decoding utility but our advice would be to ignore the demands. If you are expecting the people who encrypted your data in the first place to keep their word, you may be in for a big disappointment, as they might simply take your money. The ransom money would also likely be financing future file encoding malicious software activities. The easily made money is regularly luring more and more people to the business, which reportedly made $1 billion in 2016. A better choice would be some type of backup, which would always be there in case something happened to your files. These types of infections could happen again, and you wouldn’t need to worry about file loss if you had backup. Simply pay no mind to the demands and terminate Tron Ransomware. If you become familiar with how these threats spread, you ought to be able to avoid them in the future.
How to terminate Tron Ransomware
We warn you that you will have to obtain anti-malware program if you want to entirely terminate the ransomware. You may have chosen to erase Tron Ransomware manually but you might end up bringing about more harm, which is why we can’t suggest it. Implementing dependable removal software would be a much wiser decision because you would not be endangering your system. If the data encoding malicious software is still on your system, the security utility ought to be able to remove Tron Ransomware, as the purpose of those utilities is to take care of such infections. If you come across some kind of problem, or are not certain about how to proceed, use the below provided instructions. Unfortunately, the malware removal software will merely terminate the threat, it will not restore your files. However, free decryptors are released by malware researchers, if the file encoding malicious program is decryptable.
Download Removal Toolto remove Tron Ransomware
Learn how to remove Tron Ransomware from your computer
- Step 1. Remove Tron Ransomware using Safe Mode with Networking.
- Step 2. Remove Tron Ransomware using System Restore
- Step 3. Recover your data
Step 1. Remove Tron Ransomware using Safe Mode with Networking.
a) Step 1. Access Safe Mode with Networking.
For Windows 7/Vista/XP
- Start → Shutdown → Restart → OK.

- Press and keep pressing F8 until Advanced Boot Options appears.
- Choose Safe Mode with Networking

For Windows 8/10 users
- Press the power button that appears at the Windows login screen. Press and hold Shift. Click Restart.

- Troubleshoot → Advanced options → Startup Settings → Restart.

- Choose Enable Safe Mode with Networking.

b) Step 2. Remove Tron Ransomware.
You will now need to open your browser and download some kind of anti-malware software. Choose a trustworthy one, install it and have it scan your computer for malicious threats. When the ransomware is found, remove it. If, for some reason, you can't access Safe Mode with Networking, go with another option.Step 2. Remove Tron Ransomware using System Restore
a) Step 1. Access Safe Mode with Command Prompt.
For Windows 7/Vista/XP
- Start → Shutdown → Restart → OK.

- Press and keep pressing F8 until Advanced Boot Options appears.
- Select Safe Mode with Command Prompt.

For Windows 8/10 users
- Press the power button that appears at the Windows login screen. Press and hold Shift. Click Restart.

- Troubleshoot → Advanced options → Startup Settings → Restart.

- Choose Enable Safe Mode with Command Prompt.

b) Step 2. Restore files and settings.
- You will need to type in cd restore in the window that appears. Press Enter.
- Type in rstrui.exe and again, press Enter.

- A window will pop-up and you should press Next. Choose a restore point and press Next again.

- Press Yes.
Step 3. Recover your data
While backup is essential, there is still quite a few users who do not have it. If you are one of them, you can try the below provided methods and you just might be able to recover files.a) Using Data Recovery Pro to recover encrypted files.
- Download Data Recovery Pro, preferably from a trustworthy website.
- Scan your device for recoverable files.

- Recover them.
b) Restore files through Windows Previous Versions
If you had System Restore enabled, you can recover files through Windows Previous Versions.- Find a file you want to recover.
- Right-click on it.
- Select Properties and then Previous versions.

- Pick the version of the file you want to recover and press Restore.
c) Using Shadow Explorer to recover files
If you are lucky, the ransomware did not delete your shadow copies. They are made by your system automatically for when system crashes.- Go to the official website (shadowexplorer.com) and acquire the Shadow Explorer application.
- Set up and open it.
- Press on the drop down menu and pick the disk you want.

- If folders are recoverable, they will appear there. Press on the folder and then Export.
* SpyHunter scanner, published on this site, is intended to be used only as a detection tool. More info on SpyHunter. To use the removal functionality, you will need to purchase the full version of SpyHunter. If you wish to uninstall SpyHunter, click here.

