What is Nozelesn ransomware virus
The ransomware known as Nozelesn ransomware is categorized as a very damaging threat, due to the amount of harm it could cause. If ransomware was unfamiliar to you until now, you may be in for a shock. Ransomware encrypts data using strong encryption algorithms, and once it is done executing the process, you will be unable to open them. File encrypting malicious software is classified as a very dangerous infection as decrypting data may be not possible. You will be given the option of paying the ransom for a decryption utility but many malware specialists do not suggest doing that. Firstly, you might be just wasting your money because payment doesn’t always result in file decryption. It would be naive to believe that criminals will feel bound to aid you restore data, when they could just take your money. Additionally, that ransom money would finance future ransomware or some other malicious software. Data encrypting malicious software is already costing a lot of money to businesses, do you really want to be supporting that. And the more people give into the demands, the more of a profitable business ransomware becomes, and that kind of money surely attracts people who want easy income. Investing the money you are requested to pay into some kind of backup may be a wiser option because losing data wouldn’t be a possibility again. You can then proceed to data recovery after you delete Nozelesn ransomware or similar infections. If you have not encountered ransomware before, it is also possible you don’t know how it managed to infect your device, in which case carefully read the below paragraph.
Download Removal Toolto remove Nozelesn ransomware
How did you obtain the ransomware
You may generally see ransomware attached to emails or on questionable download site. Seeing as these methods are still rather popular, that means that users are pretty careless when they use email and download files. Nevertheless, some ransomware might use much more sophisticated ways, which need more time and effort. All crooks need to do is attach a malicious file to an email, write a plausible text, and pretend to be from a real company/organization. Topics about money can frequently be ran into as people are more inclined to care about those kinds of emails, thus open them without much thinking. It’s pretty often that you’ll see big names like Amazon used, for example, if Amazon emailed someone a receipt for a purchase that the person doesn’t remember making, he/she would open the attachment immediately. In order to safeguard yourself from this, there are certain things you have to do when dealing with emails. Check if you know the sender before opening the file attached they have sent, and if you don’t recognize them, look into them carefully. You will still need to investigate the email address, even if the sender is familiar to you. Look for grammatical or usage errors, which are generally pretty glaring in those types of emails. The way you are greeted may also be a clue, a legitimate company’s email important enough to open would include your name in the greeting, instead of a universal Customer or Member. It is also possible for ransomware to use out-of-date software on your device to infect. A program comes with weak spots that could be exploited by data encoding malware but they’re frequently patched by vendors. As has been shown by WannaCry, however, not everyone rushes to install those updates. Because a lot of malicious software makes use of those weak spots it’s so essential that you update your programs regularly. Updates could be set to install automatically, if you find those alerts annoying.
What can you do about your data
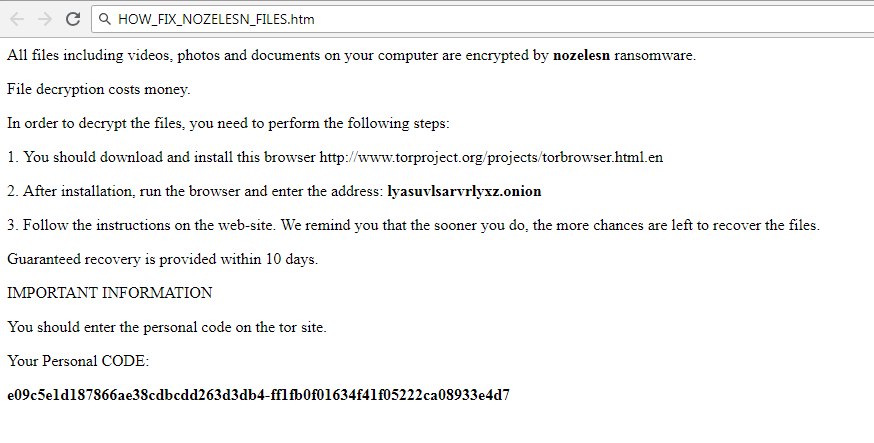
Ransomware only targets certain files, and they are encrypted as soon as they’re found. You may not see at first but when you cannot open your files, it’ll become evident that something is not right. Look for weird file extensions added to files that were encrypted, they ought to display the name of the ransomware. A strong encryption algorithm may be used, which would make data restoring rather hard, if not impossible. You’ll notice a ransom notification that will warn you that your files have been encoded and what you need to do next. You’ll be offered a decryption program, in exchange for money obviously, and crooks will warn to not use other methods because it may harm them. If the price for a decryption program is not specified, you would have to contact the crooks via email. Just as we discussed above, we do not recommend giving into the demands. Thoroughly consider all your options through, before you even consider giving into the demands. Try to recall whether you recently made copies of files but forgotten. You may also be able to locate a tool to unlock Nozelesn ransomware files for free. Security researchers may in certain cases create free decryptors, if the data encoding malware is decryptable. Before you make a decision to pay, search for a decryptor. Using the demanded sum for a reliable backup could do more good. And if backup is available, you may recover data from there after you remove Nozelesn ransomware virus, if it is still present on your computer. If you are now familiar with file encrypting malicious software’s spread ways, avoiding this kind of infection should not be hard. You primarily have to always update your programs, only download from safe/legitimate sources and not randomly open files added to emails.
Nozelesn ransomware removal
Employ an anti-malware program to get the ransomware off your device if it’s still in your device. To manually fix Nozelesn ransomware virus is no easy process and you can end up damaging your system by accident. Opting to use a malware removal program is a smarter choice. It could also prevent future file encrypting malicious software from entering, in addition to aiding you in removing this one. Once the anti-malware software of your choice has been installed, simply execute a scan of your tool and if the threat is found, allow it to terminate it. Sadly, such a program won’t help with data decryption. Once your device has been cleaned, normal computer usage should be restored.
Download Removal Toolto remove Nozelesn ransomware
Learn how to remove Nozelesn ransomware from your computer
- Step 1. Remove Nozelesn ransomware using Safe Mode with Networking.
- Step 2. Remove Nozelesn ransomware using System Restore
- Step 3. Recover your data
Step 1. Remove Nozelesn ransomware using Safe Mode with Networking.
a) Step 1. Access Safe Mode with Networking.
For Windows 7/Vista/XP
- Start → Shutdown → Restart → OK.

- Press and keep pressing F8 until Advanced Boot Options appears.
- Choose Safe Mode with Networking

For Windows 8/10 users
- Press the power button that appears at the Windows login screen. Press and hold Shift. Click Restart.

- Troubleshoot → Advanced options → Startup Settings → Restart.

- Choose Enable Safe Mode with Networking.

b) Step 2. Remove Nozelesn ransomware.
You will now need to open your browser and download some kind of anti-malware software. Choose a trustworthy one, install it and have it scan your computer for malicious threats. When the ransomware is found, remove it. If, for some reason, you can't access Safe Mode with Networking, go with another option.Step 2. Remove Nozelesn ransomware using System Restore
a) Step 1. Access Safe Mode with Command Prompt.
For Windows 7/Vista/XP
- Start → Shutdown → Restart → OK.

- Press and keep pressing F8 until Advanced Boot Options appears.
- Select Safe Mode with Command Prompt.

For Windows 8/10 users
- Press the power button that appears at the Windows login screen. Press and hold Shift. Click Restart.

- Troubleshoot → Advanced options → Startup Settings → Restart.

- Choose Enable Safe Mode with Command Prompt.

b) Step 2. Restore files and settings.
- You will need to type in cd restore in the window that appears. Press Enter.
- Type in rstrui.exe and again, press Enter.

- A window will pop-up and you should press Next. Choose a restore point and press Next again.

- Press Yes.
Step 3. Recover your data
While backup is essential, there is still quite a few users who do not have it. If you are one of them, you can try the below provided methods and you just might be able to recover files.a) Using Data Recovery Pro to recover encrypted files.
- Download Data Recovery Pro, preferably from a trustworthy website.
- Scan your device for recoverable files.

- Recover them.
b) Restore files through Windows Previous Versions
If you had System Restore enabled, you can recover files through Windows Previous Versions.- Find a file you want to recover.
- Right-click on it.
- Select Properties and then Previous versions.

- Pick the version of the file you want to recover and press Restore.
c) Using Shadow Explorer to recover files
If you are lucky, the ransomware did not delete your shadow copies. They are made by your system automatically for when system crashes.- Go to the official website (shadowexplorer.com) and acquire the Shadow Explorer application.
- Set up and open it.
- Press on the drop down menu and pick the disk you want.

- If folders are recoverable, they will appear there. Press on the folder and then Export.
* SpyHunter scanner, published on this site, is intended to be used only as a detection tool. More info on SpyHunter. To use the removal functionality, you will need to purchase the full version of SpyHunter. If you wish to uninstall SpyHunter, click here.

