About this infection
GPGQwerty ransomware is a malware that will encode your files, which goes by the name ransomware. These types of infections are not be taken lightly, as they might result in you losing your data. In addition, infecting a computer is very easy, thus making ransomware one of the most dangerous malware out there. If your system is infected, it’s quite likely you opened a spam email attachment, clicked on a malicious ad or fell for a fake download. After contamination, the encoding process will begin, and afterwards, cyber criminals will ask that you pay a ransom for data recovery. Depending on which ransomware has infiltrated your computer, the sum demanded will be different. Consider everything carefully before you agree to pay, no matter how little money it asks. There is nothing preventing cyber crooks from taking your money, providing nothing in exchange. If you take the time to look into it, you’ll certainly find accounts of people not being able to recover data, even after paying. It would be wiser to buy backup with that money. We are sure you can find a good option as there are plenty to choose from. Just uninstall GPGQwerty ransomware, and if you had made backup before the malware invaded your device, you ought to be able to restore data from there. Malware like this is lurking all over the place, and you’ll possibly get infected again, so you need to be ready for it. To keep a computer safe, one should always be ready to encounter potential malware, becoming informed about their spread methods.
Download Removal Toolto remove GPGQwerty ransomware
File encoding malicious software distribution methods
Typically, a lot of data encrypting malware use malicious email attachments and adverts, and false downloads to spread, even though you could certainly find exceptions. That does not mean more skilled cyber criminals won’t use methods that need more ability.
Since one of the ways you may have gotten the ransomware is via email attachments, try and recall if you have recently obtained a strange file from an email. Criminals distributing data encoding malware attach a corrupted file to an email, send it to hundreds of users, who contaminate their devices as soon as they open the file. We aren’t really shocked that people open the attachments, seeing as those emails might occasionally look quite genuine, mentioning money-related issues and similarly sensitive topics, which people are likely to panic about. Usage of basic greetings (Dear Customer/Member), strong pressure to open the file added, and many grammatical mistakes are what you should look out for when dealing with emails with attached files. A sender whose email is important enough to open would use your name instead of the common greeting. Amazon, PayPal and other big company names are often used because people know them, therefore are not hesitant to open the emails. Or maybe you engaged with an infected ad when browsing dubious web pages, or downloaded something from a source that you ought to have avoided. If you were on a compromised site and pressed on an infected advertisement, it could have caused the ransomware to download. Avoid untrustworthy pages for downloading, and stick to valid ones. Sources like advertisements and pop-ups are not good sources, so avoid downloading anything from them. If a program needed to update itself, it would not alert you through browser, it would either update by itself, or send you an alert through the program itself.
What happened to your files?
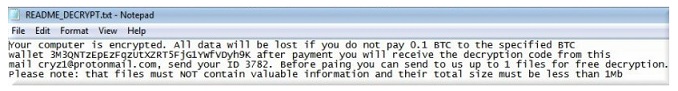
Specialists are always warning about how harmful ransomware could be, basically because infection would lead to permanent file loss. And the encoding process is rather fast, it’s only a matter of minutes, if not seconds, for all files you believe are important to become encrypted. You will notice that your files have an extension added to them, which will help you identify the data encrypting malicious software and see which files have been encrypted. Ransomware will use strong encryption algorithms, which are not always possible to break. When encryption is complete, you’ll get a ransom note, which is intended to explain to you how you ought to proceed. You’ll be offered to purchase a decryption utility, but researchers don’t advise doing that. If you’re expecting the cyber criminals accountable for encrypting your files to give you a decryptor, you may be disappointed, since they might simply take your money. Your money would also support their future criminal projects. When victims give into the requests, they are making ransomware a highly profitable business, which already earned $1 billion in 2016, and that will lure many people to it. We would recommend investing in a backup option, which would always be there in case something happened to your files. If this kind of situation occurred again, you could just remove it and not worry about potential file loss. Simply ignore the demands and erase GPGQwerty ransomware. If you become familiar with how these infections spread, you should learn to dodge them in the future.
How to remove GPGQwerty ransomware
You will have to download anti-malware utility to get rid of the infection, if it’s still somewhere on your computer. If you want to remove GPGQwerty ransomware manually, you might end up further harming your computer, which is why we cannot recommend it. A better option would be using reliable removal software instead. The tool would scan your device and if the infection is still present, it will uninstall GPGQwerty ransomware. You can find guidelines to assist you, in case you are not sure about how to proceed. The utility isn’t, however, capable of restoring your data, it’ll only terminate the infection from your device. But, you ought to also know that some data encrypting malware is decryptable, and malware specialists could release free decryptors.
Download Removal Toolto remove GPGQwerty ransomware
Learn how to remove GPGQwerty ransomware from your computer
- Step 1. Remove GPGQwerty ransomware using Safe Mode with Networking.
- Step 2. Remove GPGQwerty ransomware using System Restore
- Step 3. Recover your data
Step 1. Remove GPGQwerty ransomware using Safe Mode with Networking.
a) Step 1. Access Safe Mode with Networking.
For Windows 7/Vista/XP
- Start → Shutdown → Restart → OK.

- Press and keep pressing F8 until Advanced Boot Options appears.
- Choose Safe Mode with Networking

For Windows 8/10 users
- Press the power button that appears at the Windows login screen. Press and hold Shift. Click Restart.

- Troubleshoot → Advanced options → Startup Settings → Restart.

- Choose Enable Safe Mode with Networking.

b) Step 2. Remove GPGQwerty ransomware.
You will now need to open your browser and download some kind of anti-malware software. Choose a trustworthy one, install it and have it scan your computer for malicious threats. When the ransomware is found, remove it. If, for some reason, you can't access Safe Mode with Networking, go with another option.Step 2. Remove GPGQwerty ransomware using System Restore
a) Step 1. Access Safe Mode with Command Prompt.
For Windows 7/Vista/XP
- Start → Shutdown → Restart → OK.

- Press and keep pressing F8 until Advanced Boot Options appears.
- Select Safe Mode with Command Prompt.

For Windows 8/10 users
- Press the power button that appears at the Windows login screen. Press and hold Shift. Click Restart.

- Troubleshoot → Advanced options → Startup Settings → Restart.

- Choose Enable Safe Mode with Command Prompt.

b) Step 2. Restore files and settings.
- You will need to type in cd restore in the window that appears. Press Enter.
- Type in rstrui.exe and again, press Enter.

- A window will pop-up and you should press Next. Choose a restore point and press Next again.

- Press Yes.
Step 3. Recover your data
While backup is essential, there is still quite a few users who do not have it. If you are one of them, you can try the below provided methods and you just might be able to recover files.a) Using Data Recovery Pro to recover encrypted files.
- Download Data Recovery Pro, preferably from a trustworthy website.
- Scan your device for recoverable files.

- Recover them.
b) Restore files through Windows Previous Versions
If you had System Restore enabled, you can recover files through Windows Previous Versions.- Find a file you want to recover.
- Right-click on it.
- Select Properties and then Previous versions.

- Pick the version of the file you want to recover and press Restore.
c) Using Shadow Explorer to recover files
If you are lucky, the ransomware did not delete your shadow copies. They are made by your system automatically for when system crashes.- Go to the official website (shadowexplorer.com) and acquire the Shadow Explorer application.
- Set up and open it.
- Press on the drop down menu and pick the disk you want.

- If folders are recoverable, they will appear there. Press on the folder and then Export.
* SpyHunter scanner, published on this site, is intended to be used only as a detection tool. More info on SpyHunter. To use the removal functionality, you will need to purchase the full version of SpyHunter. If you wish to uninstall SpyHunter, click here.

