What is God Crypt Ransomware virus
God Crypt Ransomware is regarded as a dangerous threat, more often known as ransomware or file-encrypting malware. It is likely it is your first time encountering this type of malicious software, in which case, you may be particularly shocked. File encrypting malicious program encodes data using strong encryption algorithms, and once the process is carried out, data will be locked and you will be unable to open them. Ransomware is believed to be such a dangerous contamination because file decryption is not possible in every case. You do have the option of paying the ransom but for various reasons, that would not be the best idea. Paying will not necessarily guarantee that your data will be recovered, so expect that you might just be wasting your money. What’s stopping crooks from just taking your money, without giving you a decryptor. You ought to also take into account that the money will be used for malware projects in the future. Do you actually want to support an industry that costs billions of dollars to businesses in damage. Crooks are attracted to easy money, and the more victims give into the requests, the more attractive ransomware becomes to those kinds of people. You may end up in this type of situation again, so investing the requested money into backup would be wiser because data loss wouldn’t be a possibility. And you can simply erase God Crypt Ransomware without issues. Information about the most common spreads methods will be provided in the below paragraph, if you are not certain about how the ransomware managed to infect your computer.
Download Removal Toolto remove God Crypt Ransomware
Ransomware distribution methods
Rather basic methods are used for distributing file encrypting malicious programs, such as spam email and malicious downloads. There is often no need to come up with more elaborate ways because many people are not careful when they use emails and download something. That doesn’t mean more elaborate methods are not used at all, however. All cyber crooks need to do is add an infected file to an email, write some kind of text, and pretend to be from a trustworthy company/organization. You’ll frequently come across topics about money in those emails, as those types of delicate topics are what people are more prone to falling for. It is somewhat frequent that you’ll see big company names like Amazon used, for example, if Amazon emailed someone a receipt for a purchase that the person doesn’t remember making, he/she would open the attached file immediately. Because of this, you ought to be cautious about opening emails, and look out for signs that they might be malicious. If you’re unfamiliar with the sender, investigate. And if you do know them, check the email address to make sure it is actually them. Obvious and many grammar mistakes are also a sign. Another pretty obvious sign is your name not used in the greeting, if someone whose email you should definitely open were to email you, they would definitely use your name instead of a universal greeting, addressing you as Customer or Member. Weak spots in a computer might also be used by a file encoding malware to enter your computer. Those vulnerabilities in software are frequently fixed quickly after they are found so that malware can’t use them. However, as widespread ransomware attacks have proven, not all users install those patches. It is highly crucial that you regularly patch your programs because if a vulnerability is serious, Serious weak spots could be used by malicious software so make sure all your software are updated. Updates can install automatically, if you don’t wish to trouble yourself with them every time.
How does it behave
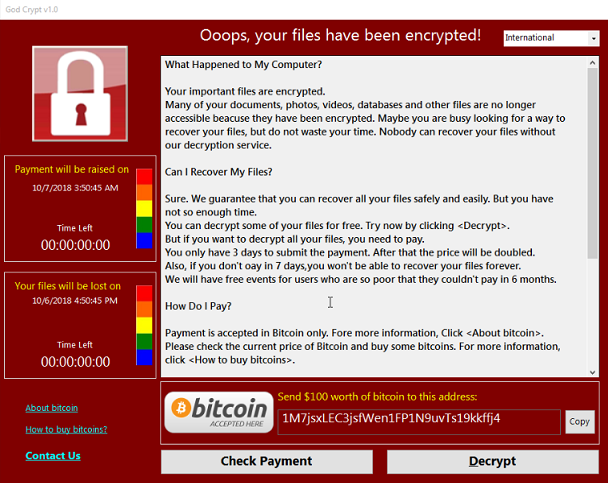
If the file encrypting malware gets into your system, it’ll look for certain file types and once it has identified them, it will encrypt them. You won’t be able to open your files, so even if you don’t notice the encryption process, you’ll know something’s not right eventually. All encoded files will have an extension attached to them, which can help people figure out the ransomware’s name. Unfortunately, file decryption might not be possible if the ransomware used a strong encryption algorithm. In the ransom note, criminals will explain what has happened to your files, and offer you a way to restore them. You’ll be requested to pay a specific amount of money in exchange for data decryption via their tool. A clear price should be shown in the note but if it isn’t, you’d have to use the given email address to contact the hackers to find out how much you would have to pay. As you’ve probably guessed, paying isn’t the option we would choose. When you have tried all other alternatives, only then should you even consider complying with the requests. Try to remember whether you’ve recently uploaded your files somewhere but forgotten. In some cases, victims can even find free decryptors. A free decryptors may be available, if the ransomware got into many devices and malicious program specialists were able to crack it. Take that option into account and only when you are fully sure a free decryption tool is unavailable, should you even think about complying with the demands. Purchasing backup with that sum may be more useful. If backup was created before the infection invaded, you can recover files after you delete God Crypt Ransomware virus. In the future, at least try to make sure you avoid data encrypting malicious software as much as possible by familiarizing yourself its distribution ways. Stick to legitimate pages when it comes to downloads, pay attention to what kind of email attachments you open, and keep your programs up-to-date.
Methods to fix God Crypt Ransomware virus
Obtain an anti-malware tool because it will be necessary to get rid of the data encoding malicious software if it’s still in your system. When trying to manually fix God Crypt Ransomware virus you might cause additional damage if you’re not the most computer-savvy person. An anti-malware tool would be a more safer choice in this case. It could also help stop these types of infections in the future, in addition to helping you remove this one. So choose a utility, install it, have it scan the computer and if the infection is located, get rid of it. Keep in mind that, a malware removal tool does not have the capabilities to restore your files. After the data encrypting malware is completely eliminated, it is safe to use your computer again.
Download Removal Toolto remove God Crypt Ransomware
Learn how to remove God Crypt Ransomware from your computer
- Step 1. Remove God Crypt Ransomware using Safe Mode with Networking.
- Step 2. Remove God Crypt Ransomware using System Restore
- Step 3. Recover your data
Step 1. Remove God Crypt Ransomware using Safe Mode with Networking.
a) Step 1. Access Safe Mode with Networking.
For Windows 7/Vista/XP
- Start → Shutdown → Restart → OK.

- Press and keep pressing F8 until Advanced Boot Options appears.
- Choose Safe Mode with Networking

For Windows 8/10 users
- Press the power button that appears at the Windows login screen. Press and hold Shift. Click Restart.

- Troubleshoot → Advanced options → Startup Settings → Restart.

- Choose Enable Safe Mode with Networking.

b) Step 2. Remove God Crypt Ransomware.
You will now need to open your browser and download some kind of anti-malware software. Choose a trustworthy one, install it and have it scan your computer for malicious threats. When the ransomware is found, remove it. If, for some reason, you can't access Safe Mode with Networking, go with another option.Step 2. Remove God Crypt Ransomware using System Restore
a) Step 1. Access Safe Mode with Command Prompt.
For Windows 7/Vista/XP
- Start → Shutdown → Restart → OK.

- Press and keep pressing F8 until Advanced Boot Options appears.
- Select Safe Mode with Command Prompt.

For Windows 8/10 users
- Press the power button that appears at the Windows login screen. Press and hold Shift. Click Restart.

- Troubleshoot → Advanced options → Startup Settings → Restart.

- Choose Enable Safe Mode with Command Prompt.

b) Step 2. Restore files and settings.
- You will need to type in cd restore in the window that appears. Press Enter.
- Type in rstrui.exe and again, press Enter.

- A window will pop-up and you should press Next. Choose a restore point and press Next again.

- Press Yes.
Step 3. Recover your data
While backup is essential, there is still quite a few users who do not have it. If you are one of them, you can try the below provided methods and you just might be able to recover files.a) Using Data Recovery Pro to recover encrypted files.
- Download Data Recovery Pro, preferably from a trustworthy website.
- Scan your device for recoverable files.

- Recover them.
b) Restore files through Windows Previous Versions
If you had System Restore enabled, you can recover files through Windows Previous Versions.- Find a file you want to recover.
- Right-click on it.
- Select Properties and then Previous versions.

- Pick the version of the file you want to recover and press Restore.
c) Using Shadow Explorer to recover files
If you are lucky, the ransomware did not delete your shadow copies. They are made by your system automatically for when system crashes.- Go to the official website (shadowexplorer.com) and acquire the Shadow Explorer application.
- Set up and open it.
- Press on the drop down menu and pick the disk you want.

- If folders are recoverable, they will appear there. Press on the folder and then Export.
* SpyHunter scanner, published on this site, is intended to be used only as a detection tool. More info on SpyHunter. To use the removal functionality, you will need to purchase the full version of SpyHunter. If you wish to uninstall SpyHunter, click here.

